It worked for me this way:
1st: create your password list
Open a txt editor and enter all possible passwords you want to try out. One password for each line. Safe that file as “passwords.txt” in the folder where you masterkey.cryptomator file is stored.
2nd: install a suitable JAVA Version
If you are sure you have Java Runtme Environment installed in version 11 or higher you can skip that. If Java RTE 11+ is not installed, you can download it for example here: https://adoptopenjdk.net/
Please read this if you struggle to find the correct version on adoptopenjdk
3rd: Download the latest release of the cracker
Download here the latest file of cracker-0.x.x-fat.jar. Right now this is cracker-0.1.1-fat.jar
Store it in the same folder where you have stored your passwords.txt file and your masterkey.cryptomator file
4th: run the tool with powershell
Assuming you are on windows, press the windows key, enter (means search) for the App “windows PowerShell” and start it.
4.1 Navigate to the folder where your file are.
You can do this by entering the following (values in [ ] have to be changed accordingly, do not type the [ ]):
cd [drive]:\[folder1]\[folder2]
In my case, the files are stored in a folder “testvault” that is stored in a folder “_eimer” that is located on my D drive. Means in my case I have to enter this to switch to this folder:
cd d:\_eimer\testvault
hit “enter” to perform the directory change
Your powershell line looks like this:
4.2: run the process
Now that we are at the right place, lets run the script.
You enter the following:
cat passwords.txt | java -jar cracker-0.1.1-fat.jar masterkey.cryptomator
press enter to run the script
4.3: see the results:
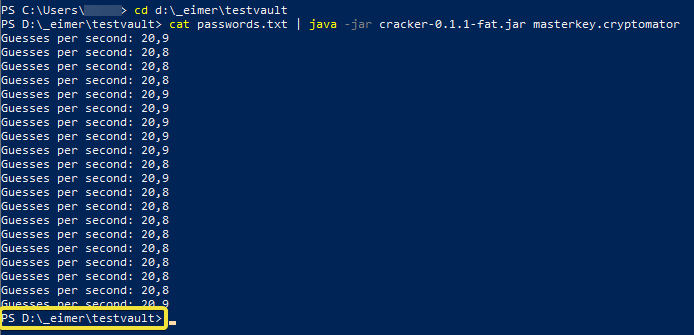
Depending how long your password list is, it will take a while until the first response is given. If it is a long password list and your system has to try hard, then you will notice a line that is showing how many attempts per second is performed. This line will be updated frequently.
Looks like this.
When you see a new Line that is starting with “PS” that means the process has finished (yellow frame). As you do not see any success message, this means there was no password in the list that was correct.
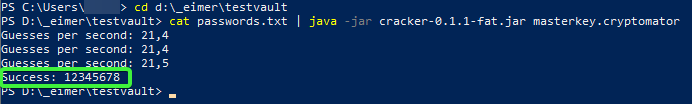
If you do have the correct password in your list, then you will receive a success message with the password. Looks like this then:
Hope this helps
PS: works well also with vault format 8 because this is all not about vault format