Hi all,
I’m new to this forum and to Cryptomator. I’m a long-time user of ‘Boxcryptor Classic’ (that is not maintained any more since years). I’m now experimenting Cryptomator. I’ve tried it on Linux (so far, so good), and now I’m exploring it on Windows (and next steps, I’ll test it on macOS and Android).
For performance reason I need to use FUSE (Cryptomator is OK in WebDAV mode but I find it too slow compared to Boxcryptor Classic).
![]() My issue
My issue
My config: Windows 10 (19042.1526), UAC enabled / Cryptomator: 1.6.5 (msi-3397) / WinFsp 1.10.22006
My vault in on a OneDrive and I’m logged as a user that is amongst the Administrator group.
When trying to access the FUSE-mounted volume and to copy or write a file into it, I am getting the error message: “You’ll need to provide administrator permission to …”.
Apparently, the issue is with the ownership of the files that is not set to be owned by those of the user who mounted the file system.
More precisely, using the default configuration (that is with “Custom Mount Flags” option unticked), all access rights are granted to an unknown user identified as S-1-0-65534.
Other groups (“Everyone” and “Authenticated users”) have only read and execute access rights. See the below screen copy.
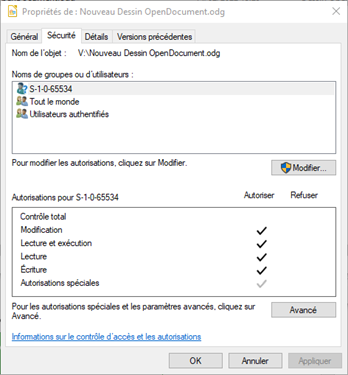
Note that using the default custom mount flags (-ouid=-1 -ogid=11 -ovolname="myVault") does not help: no change, still the same result and error message.
![]() What I tested
What I tested
I tried also with custom mount flags -ouid=-1,gid=-1. It does not solve my issue. This is translated by FUSE into user “S-1-0-65534” having all access rights and “Everyone” still having only read and execute rights. Adding the option umask=0 does not change anything.
I found in Write access denied (fuse compat layer) #40 a solution to give all access rights to “Everyone”.
If you want to just make things work, one way is to specify
-ouid=65792,gid=65792,umask=0on the command line. This should enable Full Control access to “Everyone”. [This being Windows “Everyone” is not really everyone, but for practical purposes it is.]
That will be my workaround for the time being, but that is a bit to insecure for me. Therefore I am still looking for a way to instruct FUSE to set the ownership of the files to my Windows user.
I also read in this WinFsp FAQ related to FUSE mounts a way to convert my Windows account name into a uid.
Alternatives include
-o uid=-1,gid=-1, which presents files as owned by the user and group that launched the file system and-o uid=-1,gid=11, which presents files as owned by the user that launched the file system and the group “Authenticated Users”. (Thefsptoolutility in thebinsubdirectory of the WinFsp installation directory can be used to convert Windows accounts/SID’s to UID’s and vice versa.)
So I ran the command fsptool-x64.exe -help, then fsptool-x64.exe id and identified my ‘uid’ and ‘gid’ which was in the form 3333401941. I tried the custom mount flags -ouid=3333401941,gid=3333401941 -ovolname="myVault". But it did not work.
At this stage, I’m assuming that such a value cannot (yet?) be processed by the interface.
Any idea how to solve my issue?
Thanks in advance for your help.