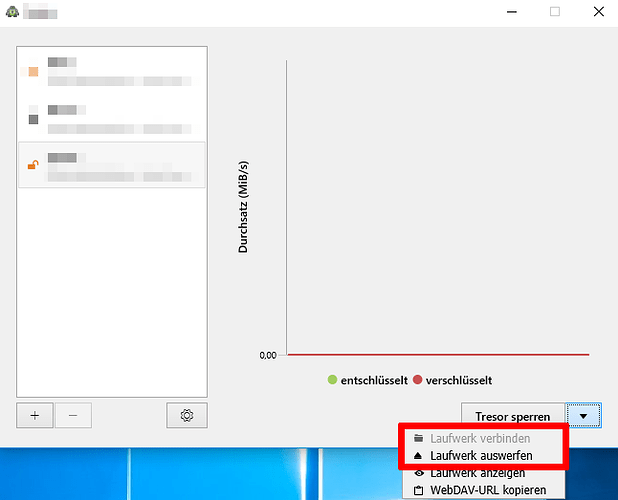
I guess you mean the WebDAV Drive. No disconnecting this drive does not lock the vault. Its a feature that you can connect/disconnect the WebDAV Drive via Cryptomator Interface. Open it, klick your vault and klick the drop down field (see screenshot). You can also use your own WebDAV Client, if you do not want to use the Windows System Client.
If you disconnect via net use, you can just connect it again via the cryptomator interface (without entering the password, as the vault is still open)
No, actually there’s no such function. A feature request is open.
The vault will be locked. Its locked as soon as the cryptomator process ends.